
Plato Version 11: the Anti-Hacker Edition
Version 11 is designed to support all the latest and best security mechanisms, while being fearfully difficult to hack
Most Plato customers are concerned about security and privacy of their systems. Apart from reputation consequences if systems are breached, privacy leaks or ransomware attacks can have serious impacts on service delivery as well as patient and staff welfare.
While earlier Plato versions were already secure, Version 11 offers an organized response to the most serious risks for a healthcare facility, such as addressing each of the OWASP Top 10 security risks to help customers keep their systems safe.
With unattended workstations and BYOD (Bring your Own Device) increasingly to be expected, V11 assists security personnel to harden their systems better than ever.
Anti-hacker features throughout V11 applications
An experienced hacker with a debugger can quickly crack an ordinary application. Plato's approach is to assume that a hacker can get hold of any executable, even for web applications where ordinary users cannot access the backend. Plato's principal has spent decades reviewing hacking and privacy and has set out to make V11 monumentally difficult to crack. Thousands of stealthy anti-hack measures are compiled into V11, intentionally difficult to detect via signature or other standard techniques. Hacking a V11 application involves stepping through literally hundreds of thousands of lines of C++ or ASM hunting for the anti-hacks... and even then the hacker might be on a wild goose chase if their activity was detected in some other section of code. This protection is seamless for users who are not trying to hack: they will see no difference in performance or features.
Database security
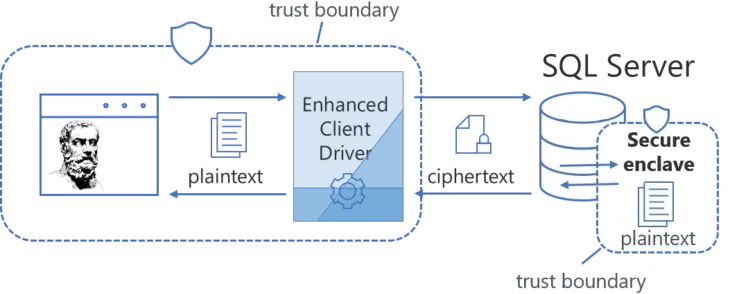
While earlier versions supported it, Version 11 defaults to Microsoft's latest "Always Encrypted with Secure Enclaves" model. This ensures that sensitive patient data is encrypted at every point outside application and enclave trust boundaries, both in transit and at rest. Even if a hacker acquires database administrator access, patient data remains protected while the usual rich Plato reporting features are still available to authorized users.
Separate Credential Database
Whether users log in via AD Integration, LDAP, OAuth2 or Plato's old login model, V11 does not decrypt connection strings or attempt access to the main database until an approved login occurs via a credential database. Even if an unauthorized hacker is able to crack the credential database, all they can access is a set of SHA-512 hashes that cannot be hacked back to credentials or used to access patient data.

OWASP Top 10
OWASP is an international collaboration to identify system risks and publish mitigations. The organization regularly publishes Top 10 lists of critical system risks. The OWASP documentation includes sets of Common Weakness Enumerations (CWEs) for each risk: For V11, Plato has reviewed the CWEs to implement every available mitigation for customer benefit.
As an example, the most critical risk in the most recent OWASP Web Top 10 is Broken Access Control. According to OWASP, in 2021 when the list was published, 94% of tested applications had some form of broken access control. So Plato has gone through the list of CWEs to ensure that every possible mitigation is in place.
Penetration Testing
Plato has Pen Testing reports for V11, but best advice is that Pen Testing is highly dependent on infrastructure. A glowing successful Pen Test in a sanitized vendor environment ought to be no more reassuring than "quality" standards and other reports that tell you nothing about your own risk. Plato can assist customers interested in Pen Testing in their own systems and can furnish CWE mitigation reports identifying areas where site Pen Testing is most advantageous.
Deployment Models
Plato was an early adopter of browser/web applications in the mid 1990s, but more recently Plato reverted some apps back to dedicated Windows executables and dlls, to mitigate certain risks. V11 deployment models include not only browser-based but also apps running locally or from an application server, apps run via Citrix or RDP (Remote Desktop Protocol) or similar, or as a Remote Desktop App that appears to run on a user's PC but actually is running on a secure server. Many customers already have sophisticated remote access provisions so it can be more efficient and safer to deliver an application in this environment than to deploy and configure a web application. If web apps are used, the V11 installer correctly configures application folders and Internet Information Server settings for robust security, while the web apps themselves can detect and prevent cross-site or injection attacks, request forgery, url manipulation and other devious hacks that can be attempted via browser.
Delivery
V11 will be delivered for production use in mid-2025. The intention is that with the next OWASP reports due by March 2025, Plato prefers to provide customers with one V11 release referencing 2025 risks and CWEs, rather than deploying for the current 2021 lists only to see everything changing months later. Customers who have other reasons to deploy V11 now can contact Plato to access Release Candidates in advance of the formal delivery.